Digital Violence: How the NSO Group Enables State Terror
Visit the DIGITAL VIOLENCE platform here.
Listen to a sonic interpretation of the data by Brian Eno.
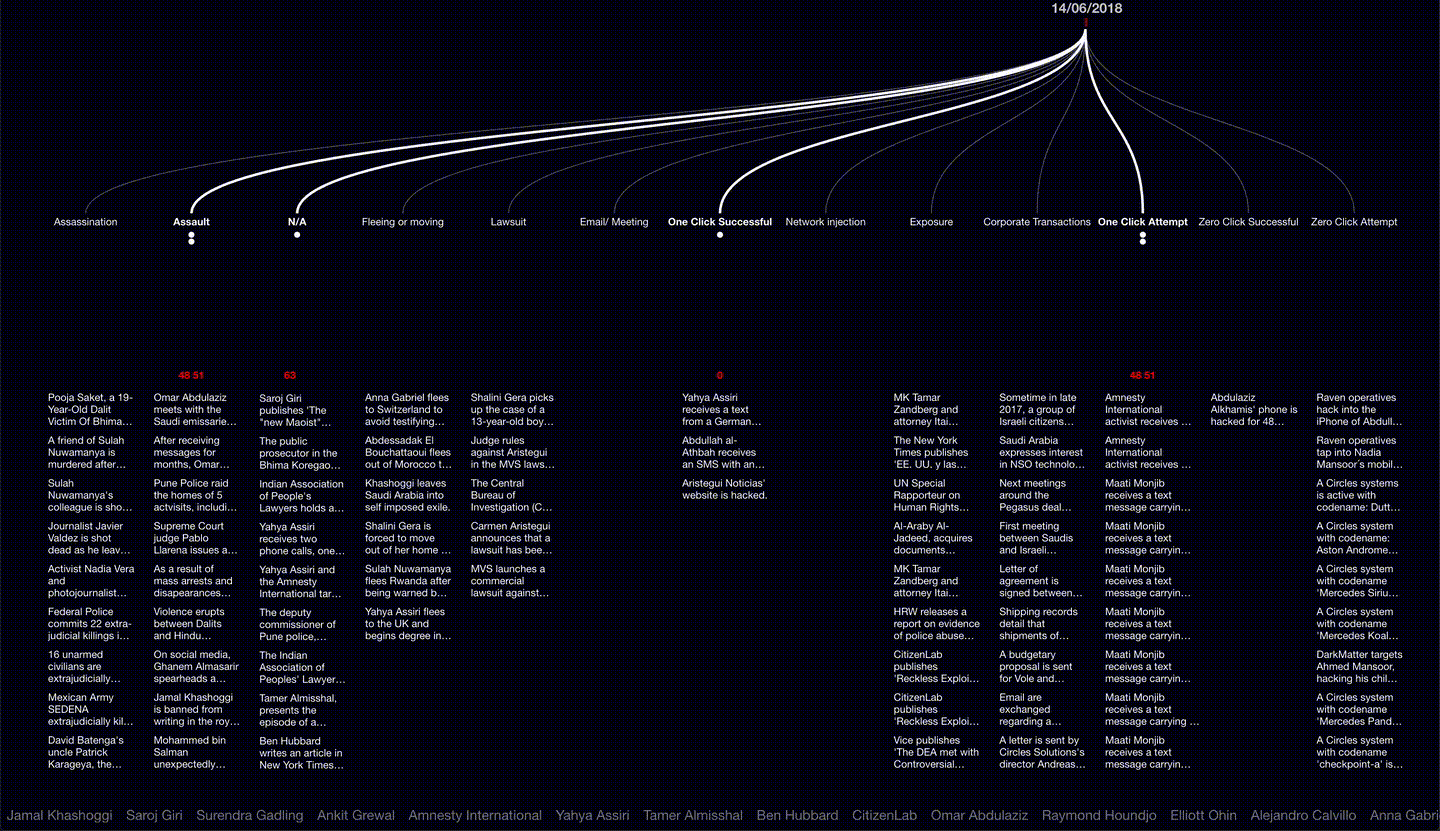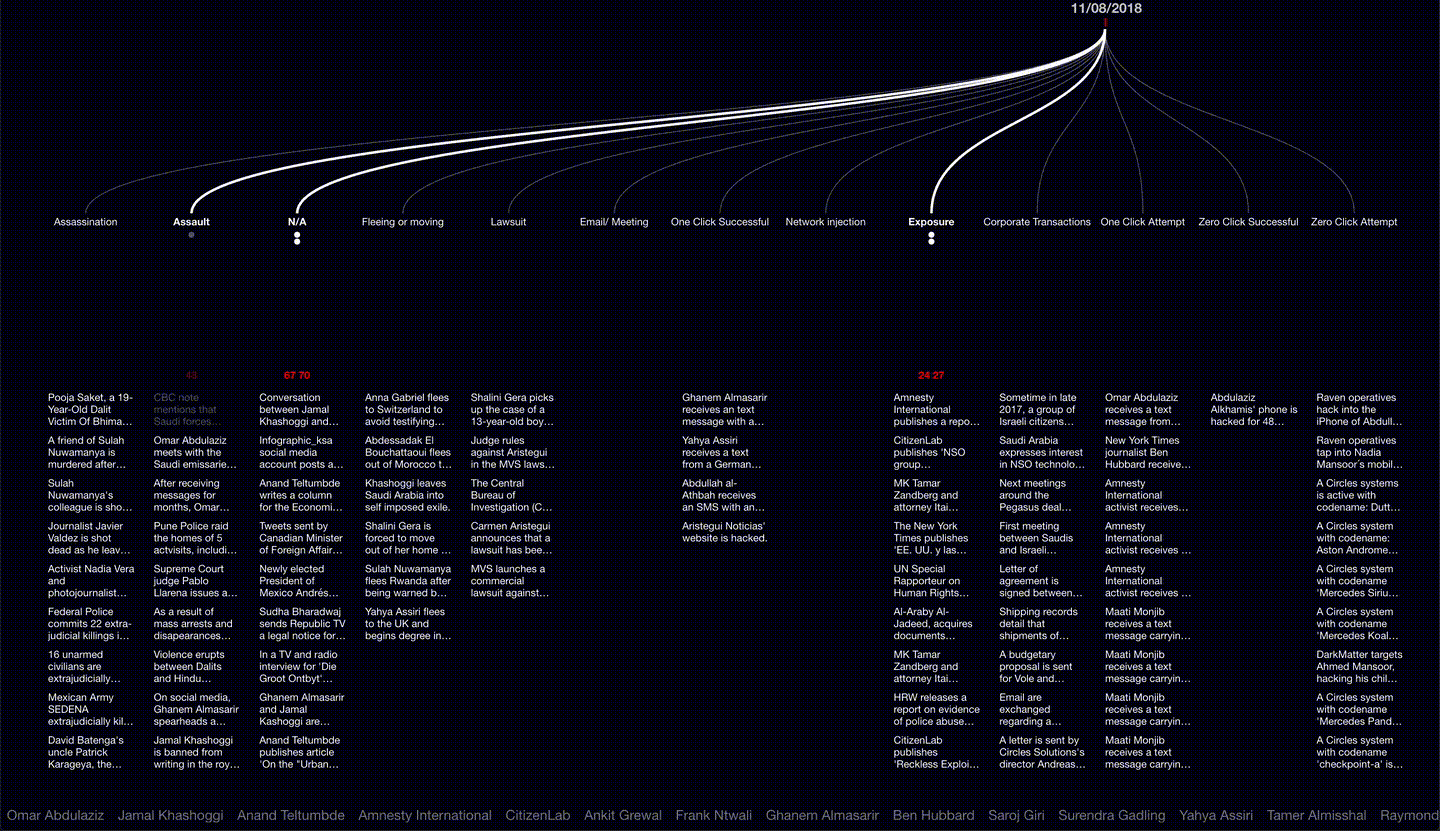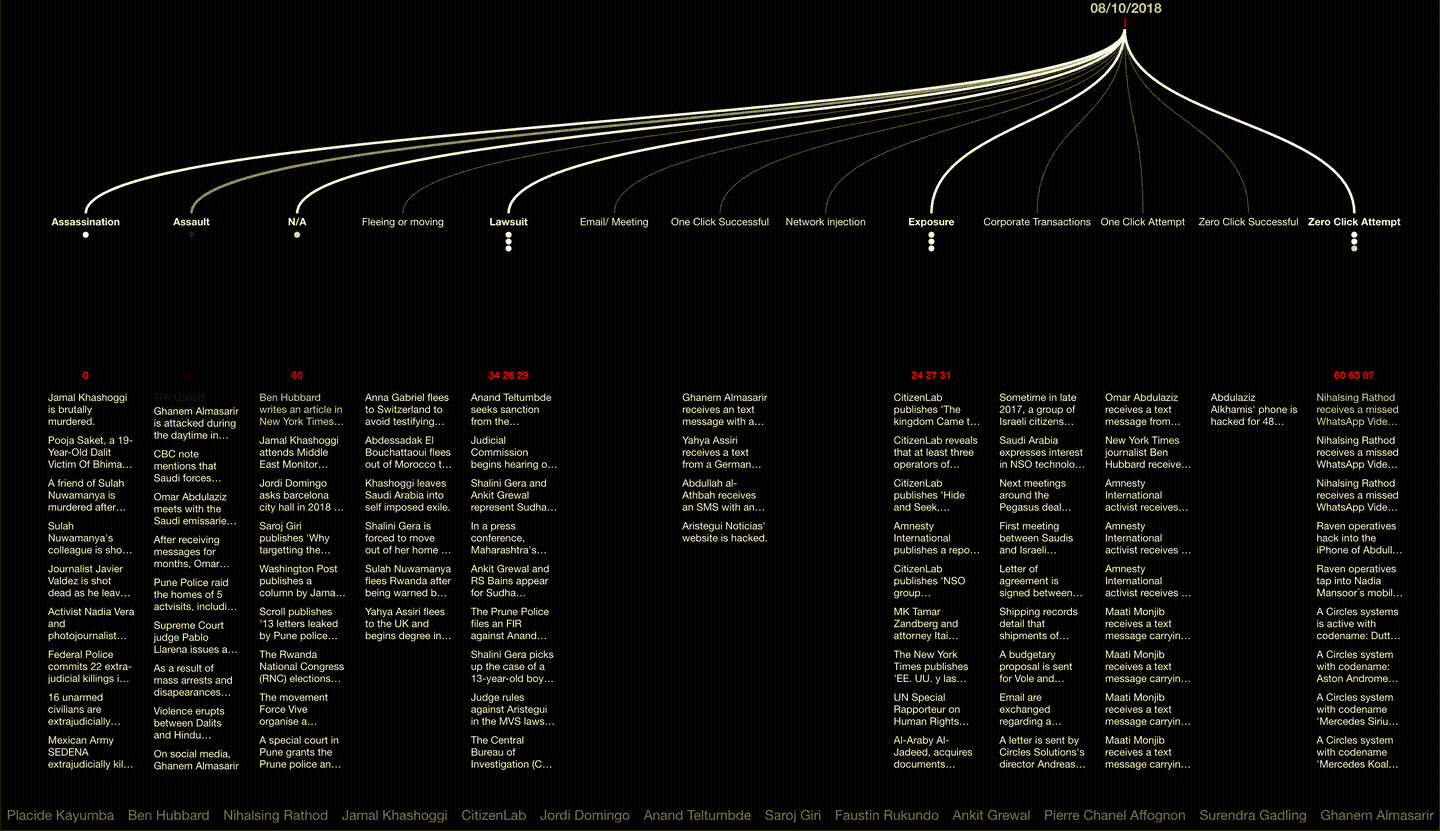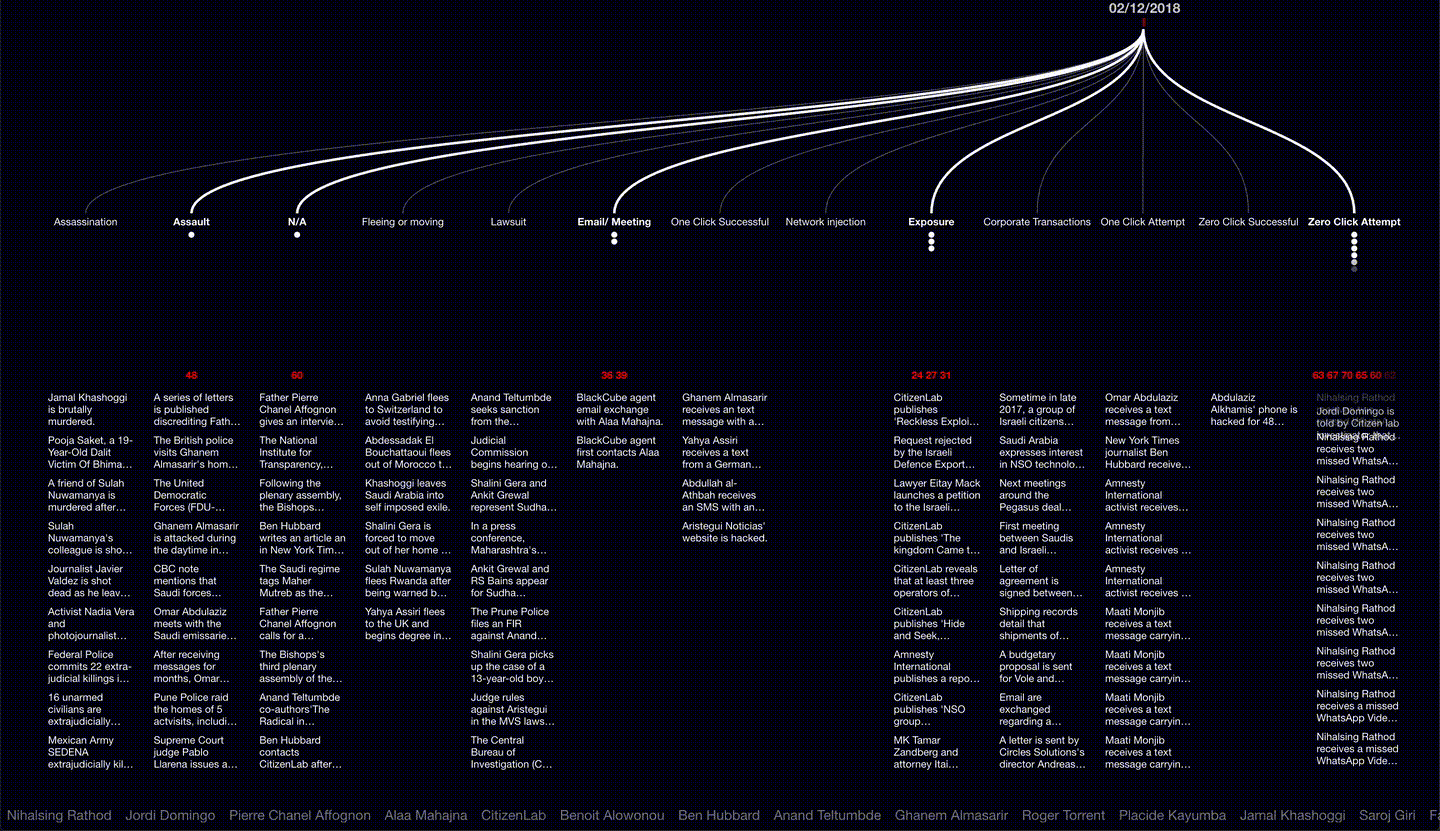
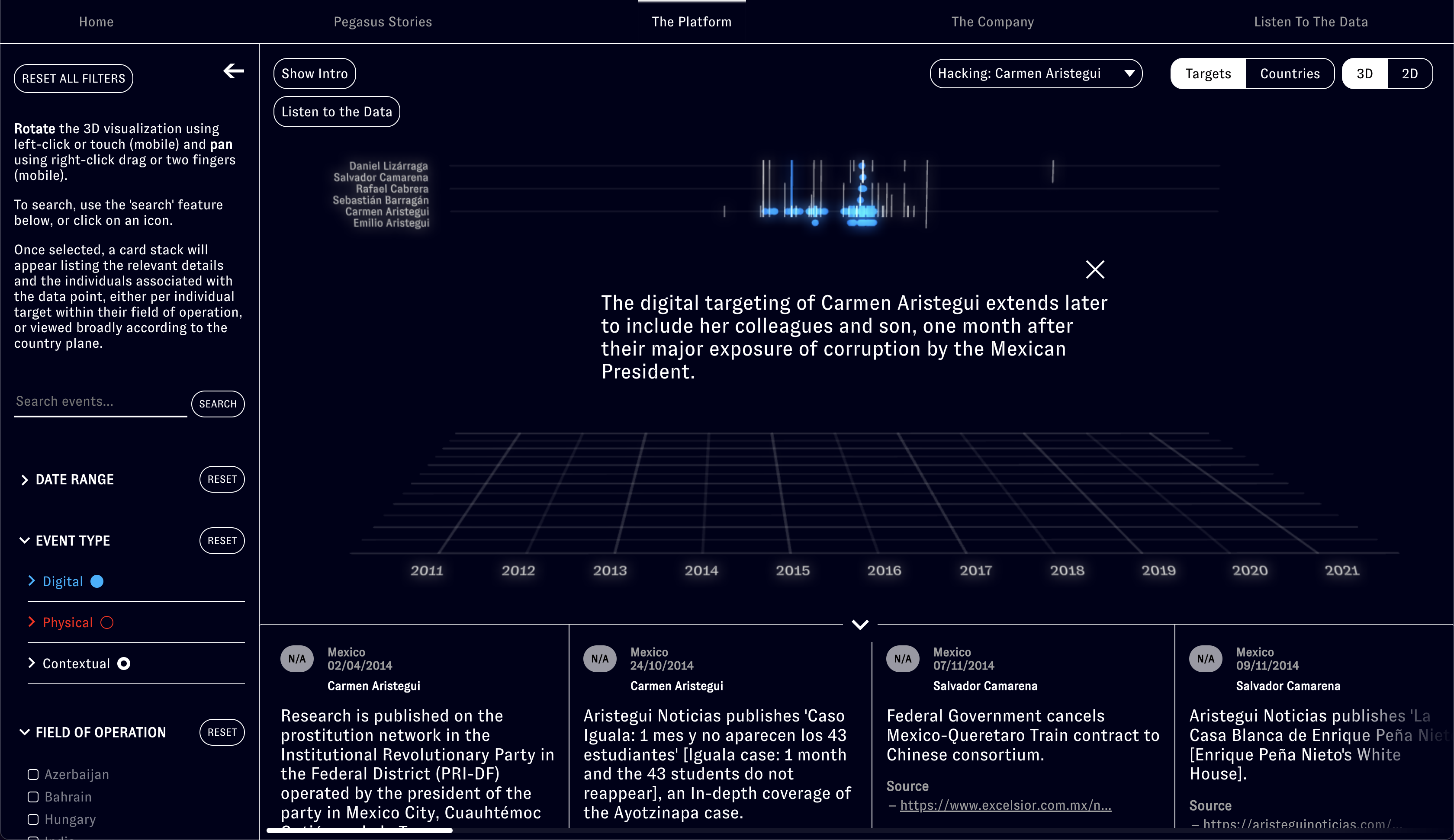
First detected in 2015, the NSO Group’s Pegasus malware has reportedly been used in at least 45 countries worldwide to infect the phones of activists, journalists and human rights defenders. Having learnt that our former collaborators and close associates were hacked by Pegasus, Forensic Architecture undertook 15 months of extensive open-source research, interviews assisted by Laura Poitras, and developed bespoke software to present this data as an interactive 3D platform, along with video investigations narrated by Edward Snowden to tell the stories of the individuals targeted and the web of corporate affiliations within which NSO is nested. Supported by Amnesty International and the Citizen Lab, our analysis reveals relations and patterns between separate incidents in the physical and digital sphere, demonstrating how infections are entangled with real world violence, and extend within the professional and personal networks of civil society actors worldwide.
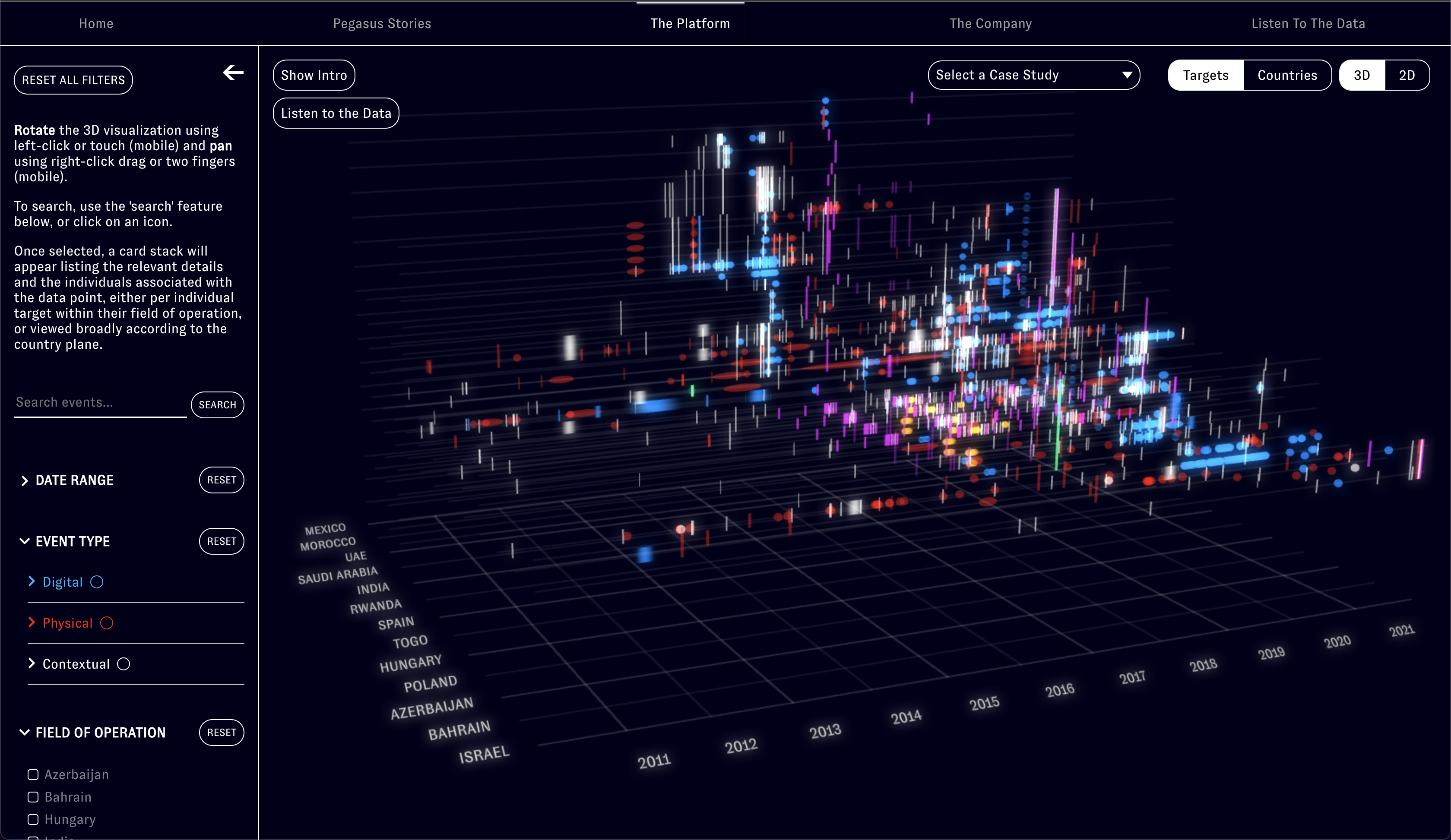
NSO Group Technologies Ltd. was founded in Israel in 2010 by Niv Carmi, Shalev Hulio and Omri Lavie. Part of an ecosystem of Israeli cyber-weapons companies—developed in the context of its ongoing occupation and settler-colonial surveillance of Palestinians—NSO’s Pegasus malware has reportedly been used since at least 2015 in at least 45 countries worldwide to infect the phones of activists, journalists and human rights defenders.
Forensic Architecture’s interest in the NSO Group dates back to 2017, when reporting by The Citizen Lab revealed that members of Centro Prodh, our collaborators in investigating the disappearance of 43 students from Ayotzinapa, Mexico, had been hacked using Pegasus.
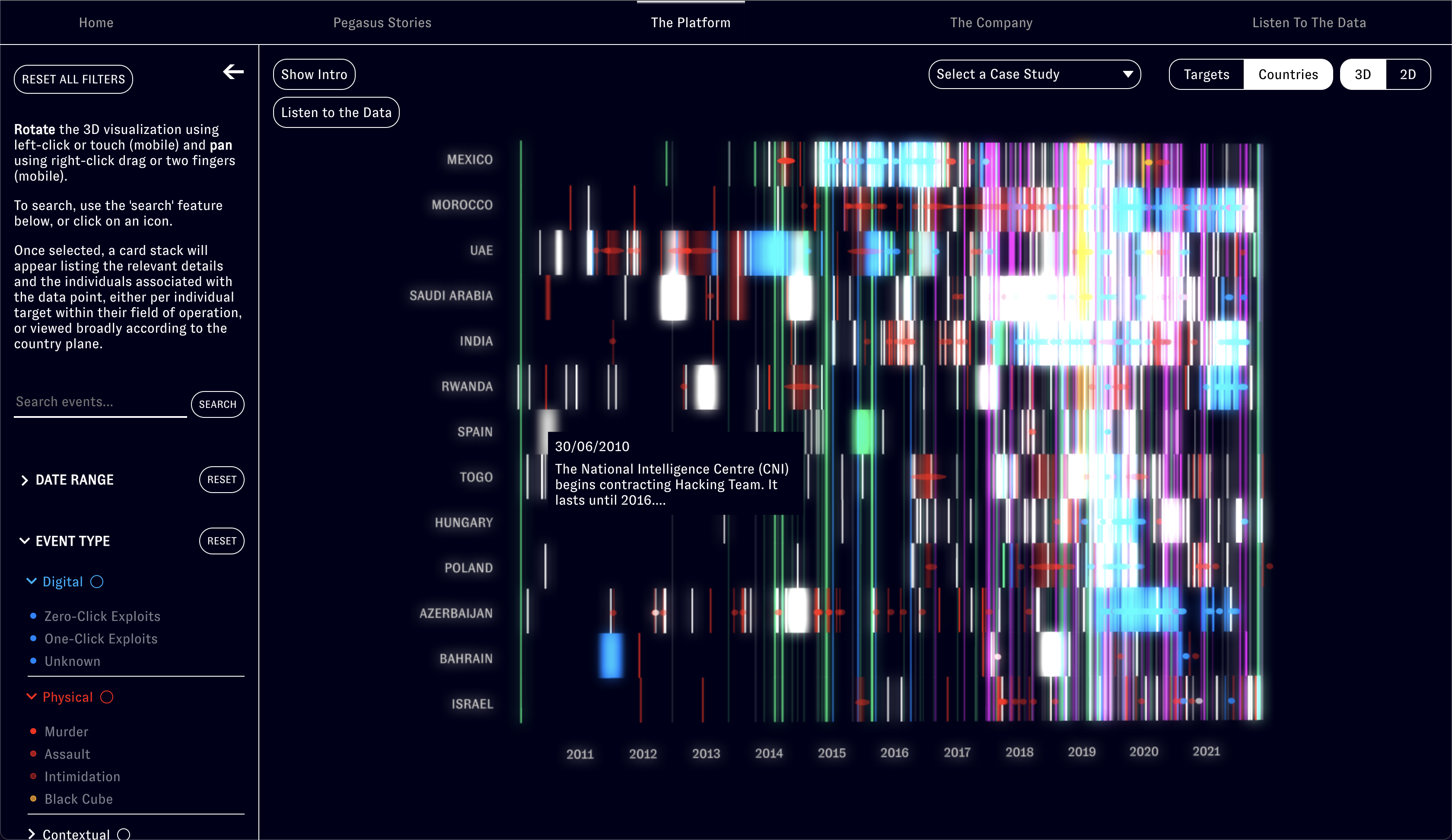
The investigation into NSO Group began two years later, when Forensic Architecture learnt that our close associates, members of the legal team leading a suit against NSO on behalf of a number of human rights defenders, were informed by WhatsApp in 2019 that their phones had also been infected.
While reporting on this issue incrementally exposed new cases of infection, we undertook this project in order to provide the public, researchers and the legal team with a general tool to explore relations among different types of NSO-related activities worldwide.
NSO has yet to confirm a single state or corporate client, and continues to receive security export licences from Israel’s Ministry of Defence for the sale of Pegasus—despite being challenged in Israeli and international courts.
The investigation consists of:
A navigable digital platform, Video investigations to tell the stories of human rights defenders from around the world reportedly targeted by Pegasus, and An interactive diagram and video presenting new research into the web of corporate affiliations within which the NSO Group is nested. With this, Forensic Architecture has for the first time mapped the global landscape of NSO-related activities to demonstrate new connections and patterns between ‘digital violence’ using Pegasus and real-world violence directed at lawyers, activists, and other civil society figures.